Imagine you’re closing a big deal with a Fortune 500 client. Everything looks good until they ask, “Are you SOC 2 compliant?” If you can’t answer with confidence, that deal might slip away.
By 2025, with a threat landscape that evolves daily and customer trust is challenging to acquire, SOC 2 compliance has become the new baseline for doing business for SaaS, cloud services, fintech, and digital health vendors.
SOC 2 is not merely a checklist of compliance or preparation for an audit. It’s a framework that demonstrates your organization's commitment to data protection, system reliability, and client privacy.
This blog is your complete guide to what SOC 2 compliance is, why it’s more relevant than ever in 2025, and how your service business can benefit from it.
What is SOC 2 Compliance?
SOC 2 - Service Organisation Control 2 is a framework that was developed by the American Institute of Certified Public Accountants (AICPA) in 2010 for service organisations that store, process, or transmit customer data in the cloud.
While other security frameworks emphasize the technical aspects of setting up a system, SOC 2 focuses primarily on the operational processes involved.
SOC2 builds on a framework with five “Trust Service Criteria.” Those are: Security, Availability, Processing Integrity, Confidentiality, and Privacy.
The primary goal of the SOC2 framework is to verify that companies have reasonable controls to protect data. In short, SOC 2 compliance is the evidence that a company can be trusted to protect your data.
{{cta-image}}
{{blog-cta-1}}
Principles of SOC 2
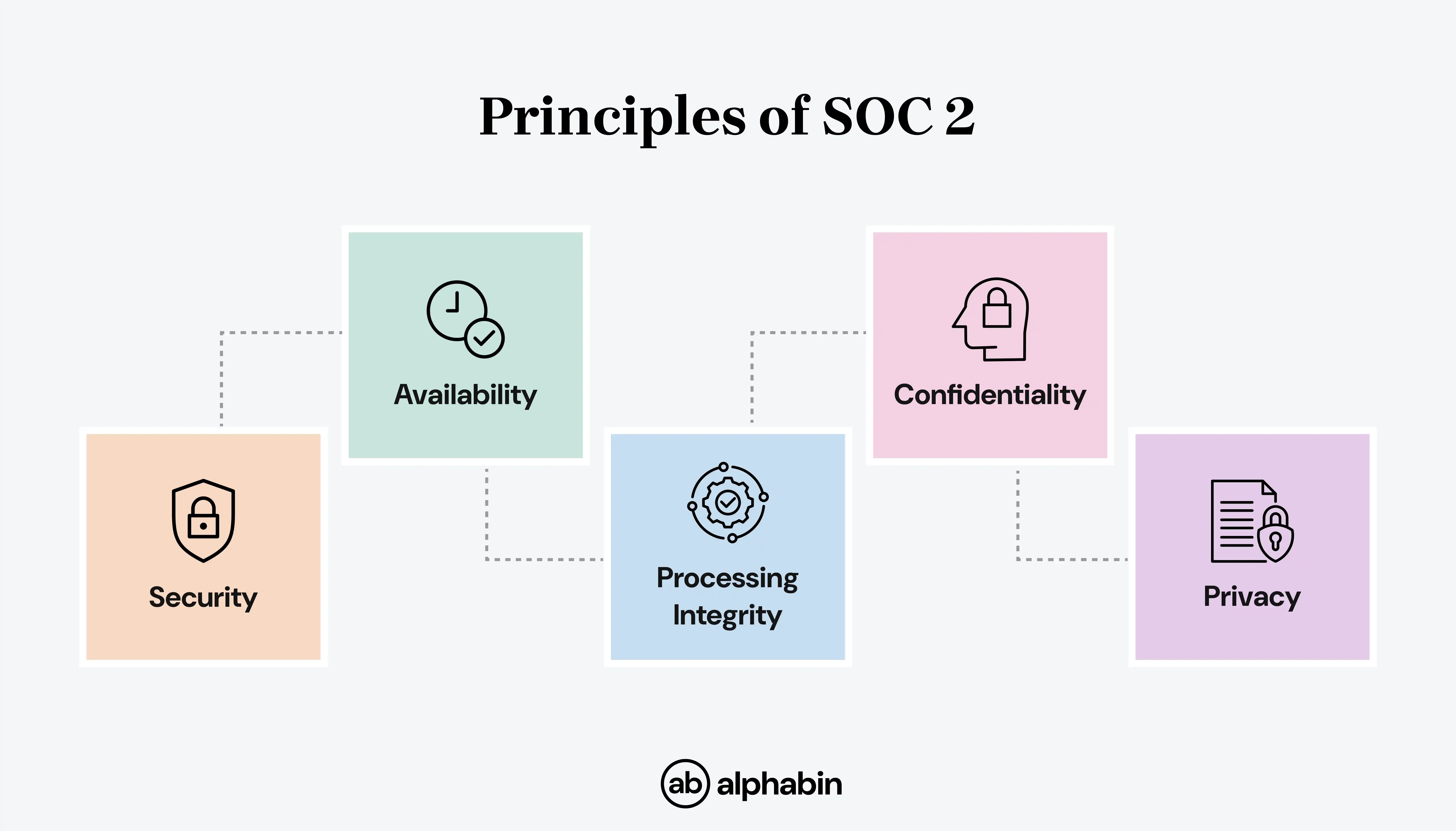
SOC 2 is based on five key principles that are collectively known as "trust service criteria."
Security: Ensures that the system is protected against unauthorized physical and logical access.
Availability: ensure that the system and its data are available for operation as contracted.
Processing Integrity: The processing of any system is complete, valid, accurate, timely, and authorized.
Confidentiality: Information designated as confidential will be protected as committed or agreed.
Privacy: ensures that Personal information or personal data are collected, used, and handled properly under privacy principles and regulations.
SOC1 vs SOC2 vs SOC3
SOC2 Compliance: Type I and Type II Reports
SOC 2 compliance has two types of reports: Type 1 and Type 2.
What are Type 1 and Type 2 reports?
SOC 2 Type I
This report looks at your controls at a point in time and essentially verifies that your security policies and systems are indeed in place right now.
In effect, it is a snapshot, verifying that controls are designed appropriately and have been operationalized.
However, it does not test and verify whether those controls are operationalizing as intended over time.
SOC 2 Type II
This report takes it one step further. It verifies that those controls are indeed operationalized and are working as intended over time.
Type II report demonstrates evidence that your controls not only operationalize as intended on paper, but function in practice, day after day, over the course of time.
More specifically, the Type 2 audit includes detailed testing of control activities, verifying that controls were operationalized over the audit testing period, as well as verifying that exceptions to the controls have been appropriately actioned.
{{blog-cta-2}}
What makes it different?
Many customers and prospects prefer Type 2 reports because they show reputable and consistent security practices rather than just good intentions.
Why SOC 2 Compliance Matters More in 2025?
SOC 2 compliance matters more now in 2025 because of increased cyber threats, the importance of data security for businesses, and a greater need to establish trust with customers and business partners.
It has already become a necessity, not only for SaaS companies but for any business that handles sensitive data.
Benefits of being SOC 2 Compliant
SOC 2 compliance delivers several benefits for the organization, primarily showing commitment to strong data security and trust with customers and partners.
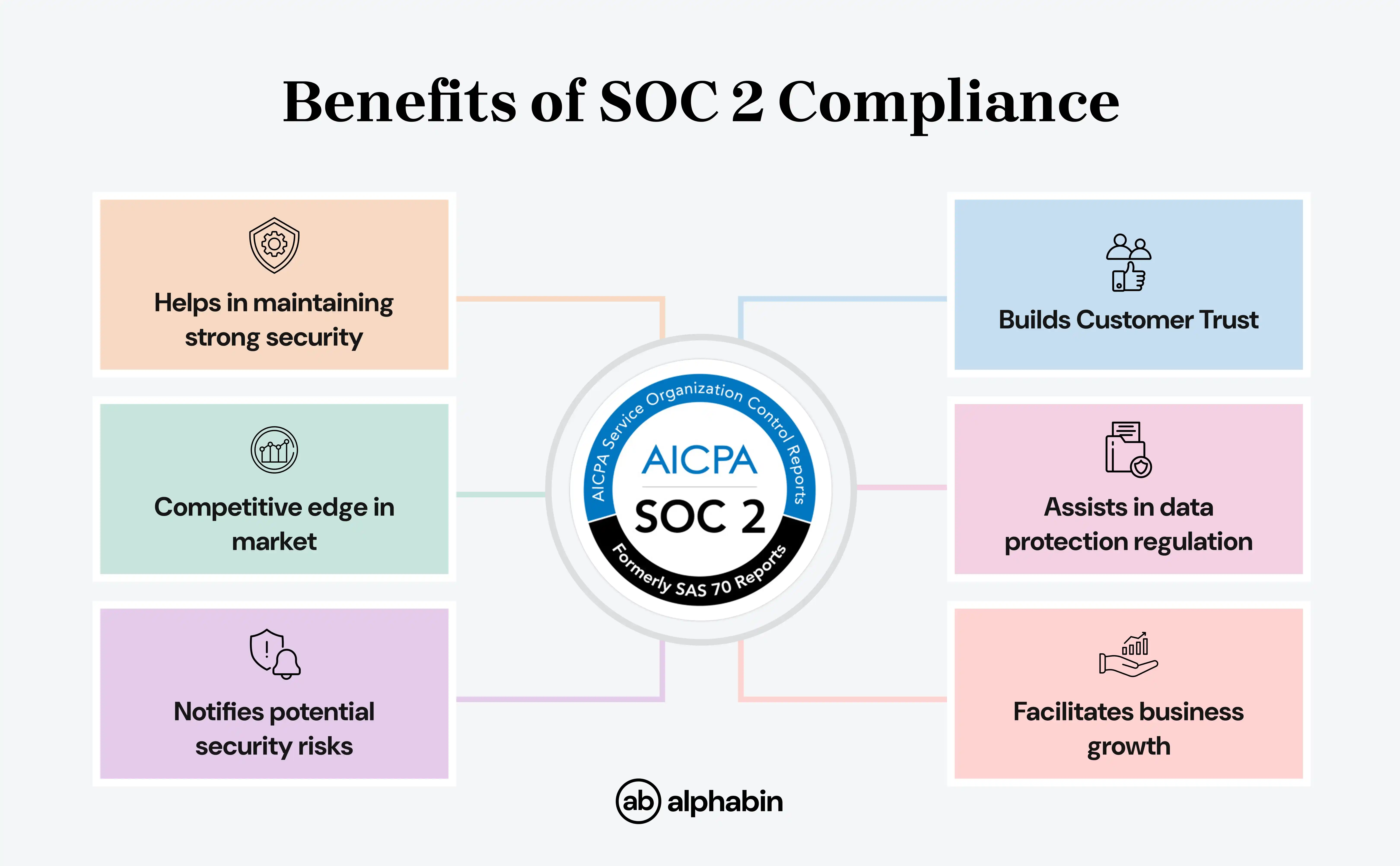
Why do you need SOC 2 in 2025?
When it comes to 2025, SOC 2 compliance will be increasingly essential for any service organization processing customer data to demonstrate a continued commitment to security and trust with clients and partners.
In the end, compliance will provide an organization with the opportunity to have a more mature security infrastructure, identify revenue streams, and pursue projects requiring organizations to obtain compliance.
- AI and Machine Learning: As you add AI monitoring and advanced threat detection, SOC 2 is the framework to ensure it’s done securely.
- Zero-Trust: Modern security requires validation of every access request. SOC 2 matches zero-trust principles.
- Remote Work: With remote teams here to stay, SOC 2 ensures security practices are consistent across all work environments.
- Supply Chain: Customers are looking at their vendors’ security practices. SOC 2 offers the demanded transparency.
- Data privacy regulation: As privacy legislation becomes increasingly global, SOC 2’s criteria for privacy provide organizations with a way to comply with a range of jurisdictions.
SOC2 Compliance: Tools and Platforms
Achieving SOC 2 compliance will require tools and platforms that can manage controls around security, automate processes, and streamline the audit process.
Going modern in SOC 2 compliance doesn't have to be a manual disaster. The right tools can handle a lot of the heavy lifting automatically.
Compliance automation tools
- Drata: Monitors continuously, collects evidence automatically, and sends real-time alerts to keep your SOC 2 controls on track, for scaling companies looking for hands-off compliance that grows with them.
- Vanta: Automates compliance tasks and integrates with HITRUST CSF, perfect for healthcare and SaaS companies.
Simplifies vendor risk management with customizable workflows. - Secureframe: Walks you through SOC 2 readiness with policy templates and AI-powered issue resolution. Also helps in fixing gaps quickly.
- Sprinto: For high-growth teams needing strong automation and support for several frameworks like SOC 2, ISO 27001, and GDPR Compliance.
- DuploCloud: Automates SOC 2 controls into your DevOps workflows, saving engineering time.
For cloud-native teams who want security without slowing development.
{{blog-cta-3}}
SOC2 Audit: What you Need to Know?
A SOC 2 audit is an assessment done by an audited professional who checks that the company protects customer data properly and safely.
The audit verifies how a company secures data, who can access that data, and verifies that they have the appropriate security processes in place.
Upon successful completion of the audit, the organization receives a SOC 2 report, which provides clients and partners with assurance that they can have confidence in the organization's systems.
In short, view a SOC 2 audit as a report card signifying the care and seriousness the organization gives to data protection.
Who can perform a SOC 2 audit?
Only licensed CPA firms or firms approved by the American Institute of Certified Public Accountants (AICPA) can complete SOC 2 audits.
The auditor or auditing firm also must be an independent certified public accountant (CPA), which means they are not associated with the service organisation they conduct the audit for.
Not all CPAs are qualified to conduct these audits. Qualified Auditors Are:
- Licensed CPAs with experience in SOC reporting
- CPA firms specializing in SOC audits
- Auditors trained and certified in Trust Service Criteria
SOC2 audit process: step-by-step
Step- 1: Define your scope
- Decide what systems, processes, and data will be included in your audit. Determine which Trust Service Criteria to include.
- Security is required, but then you have the choice to include Privacy, Confidentiality, Availability, or Processing Integrity based on your type of business and client expectations.
Step- 2: Organise your internal policies and controls
- You'll need to have written security policies, such as access controls, encryption standards, incident response plans, and documented technical controls to have a completed SOC 2 audit.
- You can use internal controls to show how you're adequately and consistently protecting data across your organization, as stated in your policies and procedures.
Step- 3: Conduct readiness assessment
- Readiness assessments basically mean mock audits, and they help you find any gaps or weaknesses before the actual audit.
- You can conduct them yourself, or you can have a consultant perform them.
Step- 4: Select an Auditor
- SOC 2 audits must be performed by an independent CPA firm that is properly accredited through the AICPA.
- Identify an compliance auditor or firm that has experience within your industry because they will thoroughly review your documentation, processes, and systems to prepare your report.
{{cta-image-second}}
Step- 5: Go through the audit
- For Type I, the auditor will look for one thing. Have your company's controls been designed and put in place on the selected date?
- For Type II, the auditor will consider how well those controls have been in place and worked over a while (typically 3 to 12 months).
- Plan on being interviewed, document reviewed, system walkthroughs, and evidence collected.
Step- 6: Receive your SOC 2 report
- When the audit is complete, you will end up with a SOC 2 report, which includes a description of your system, the auditor's opinion, and the results of their testing.
- This report is what you are supposed to share with customers or partners and will show that your organization is at a respectable level of industry performance in terms of data security and reliability.
Step 7: Continue to Monitor Compliance
- Once you receive the audit report and review it, the work is not done.
- You should keep monitoring your systems, updating your policies, training staff, and planning your annual re-audits (especially if you are SOC 2 Type II).
- Tools like Alphabin can monitor in a very streamlined way and notify you in real-time about policy violations or lack of compliance.
Why Should SaaS Have SOC2 Certification?
Obtaining SOC 2 certification is a valuable benefit to SaaS companies as it shows a strong commitment to data security and enhances customer and potential customer trust.
It also helps SaaS Vendors stay compliant with their vendor requests, to gain competitive advantages and mitigate risk associated with data breaches or compliance industry standards violations.
Essentially, it reinforces to clients that the SaaS company has strong security controls to safeguard sensitive information.
{{cta-image-third}}
Choosing SOC2 compliance partner
Prioritize experience, expertise, and a strong case history of success when looking for a SOC 2 compliance partner.
Consider these important points when choosing a SOC 2 compliance partner:
Customisation: Consider a partner who has solutions that can be customised to your circumstances and risk appetite.
Integration: Check that the partner's solutions will connect to devices and systems that you already have in place.
Cost-efficiency: While price matters, valued experience and quality mean more than the price alone.
Transparency & Communication: Choose a partner that you can engage with openly and transparently.
Conclusion
SOC 2 compliance has moved beyond a standard for security to become a critical signal of trust for cloud-centric companies. By 2025, SOC 2 certification will often keep non-certified companies from closing sales, failing vendor reviews, or losing business altogether.
Achieving compliance certification will be a competitive differentiator, and you will create a more secure organization. For service-centric companies, it will help you in long-term growth as a measure of credibility.
Start your SOC 2 journey with Alphabin, and grow your business in a trust-driven economy.
FAQs
1. How much does SOC 2 cost?
Costs vary greatly depending on organizational size and complexity, and can range in price from $15,000 to $100,000+ for audit fees and implementation costs.
2. Do I need all five trust service criteria?
Security is mandatory for any SOC 2 audit. The other four criteria (Availability, Processing Integrity, Confidentiality, Privacy) are up to you and based on your business needs.
3. How often do I need to renew SOC 2?
Most organizations refresh their SOC 2 reports on a yearly basis so as to maintain their current certification status.
4. What’s the difference between SOC 2 and ISO 27001?
SOC 2 is focused on data and is popular in North America; ISO 27001 is a broader information security management system standard used globally.



.svg)









%20(1).webp)