At 2:30 AM, Dr. Sarah Chen’s phone rang with the call every healthcare worker dreads: a data breach at her small dermatology clinic. Over 1,200 patient records were exposed.
The worst part? The breach could have been prevented using simple HIPAA safeguards.
These stories occur hundreds of times each year in various healthcare organizations. And in 2025, the stakes are even higher.
The Department of Health and Human Services has implemented more audits and taken violations of HIPAA compliance more seriously; therefore, practices can no longer miss violations in compliance.
The HIPAA compliance checklist below will assist your practice, whether you're a solo provider or part of a major health organization, to be audit-ready, safeguard patient-specific data, and eliminate some apparent risks, even in 2025 and beyond.
What is HIPAA Compliance?
HIPAA (Health Insurance Portability and Accountability Act) compliance involves adhering to federal regulations that ensure the safekeeping of patient health information.
It provides national standards to protect Protected Health Information (PHI) and provides patients' rights to their medical records.
Under HIPAA, PHI can be any written medical record, lab results, X-rays, bills, and even conversations that include identifiable health information.
This means any instance of patient data, from booking the appointment to billing, has protocols that are safeguarded.
The goal is to:
Keep patient privacy protected: to secure the privacy of the health information of individuals.
Secure electronic health records: to ensure appropriate safeguards to protect the confidentiality, integrity, and availability of electronic PHI (ePHI).
Allow the healthcare operations to occur: to permit appropriate information sharing, when needed, for treatment, payment, and healthcare operations.
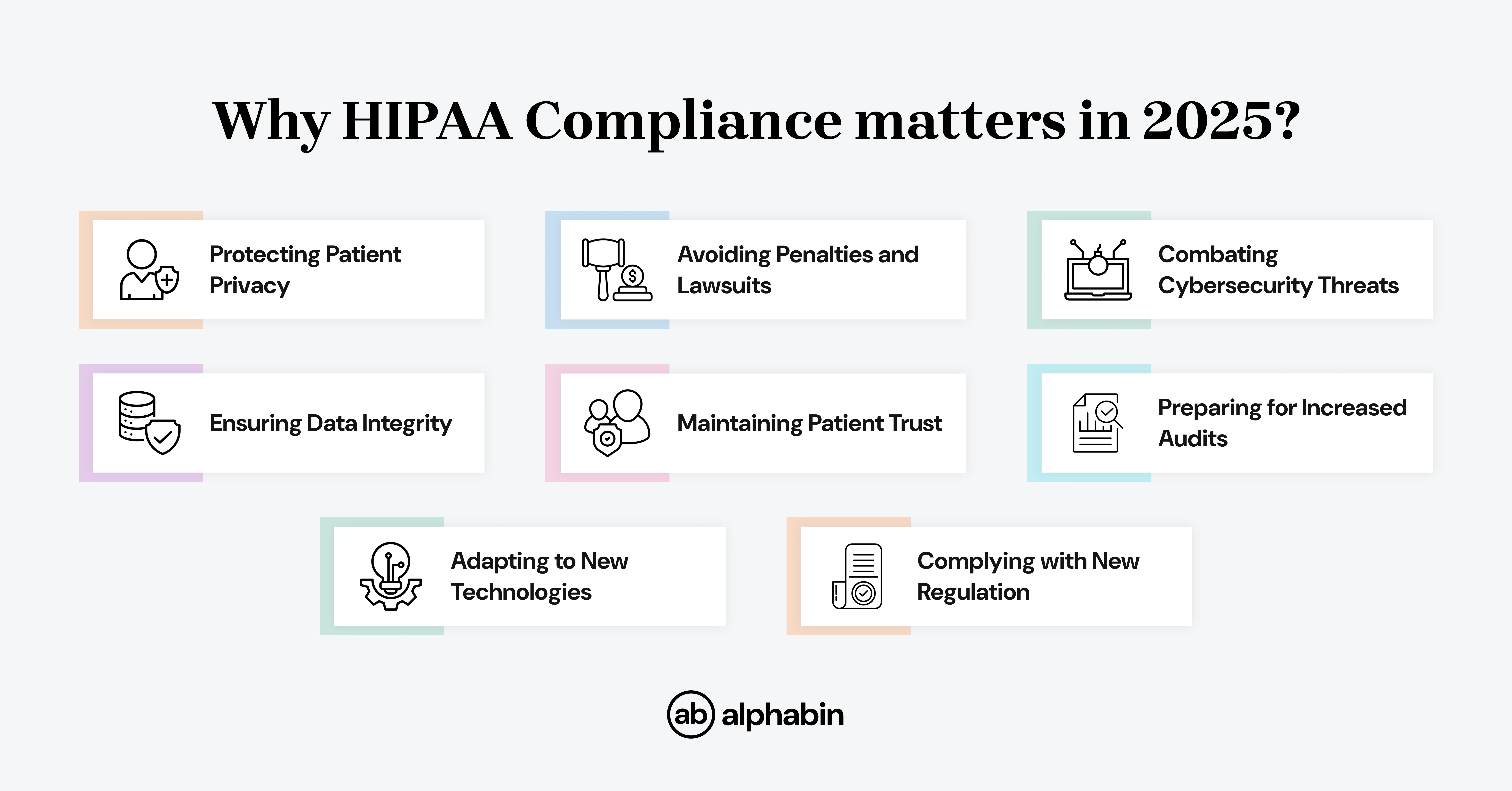
Why does it matter in 2025?
HIPAA compliance is still important in 2025 due to Cybersecurity threats, increased data breaches, and changing rules are still a reality.
Protecting patient information, avoiding penalties, and protecting reputation are all reasons to stay compliant.
Penalties of Non-Compliance
Non-compliance with HIPAA has serious consequences that can be as alarming as fines, civil liability, or even criminal acts of prosecution.
HIPAA violations can be identified through internal reviews or a HIPAA audit, either of which may result in penalties if non-compliance is found.
The penalties for non-compliance will vary based on the seriousness of the violation and generally, from a less serious violation to an intentional violation.
With that in mind, in 2025, non-compliance with HIPAA could entail monetary fines and/or imprisonment based upon the seriousness and nature of the violation.
Civil penalties (HHS Office for Civil Rights — inflation-adjusted amounts effective Aug 8, 2024):
HHS uses a four-tier civil penalty scheme based on the degree of culpability. The inflation-adjusted penalty amounts per violation (and caps per calendar year for multiple identical violations) are as follows:
Tier 1 — No knowledge (did not know act/omission was a HIPAA violation): $141 to $71,162 per violation; calendar-year cap: $2,134,831.
Tier 2 — Reasonable cause (not willful neglect): $1,424 to $71,162 per violation; calendar-year cap: $2,134,831.
Tier 3 — Willful neglect, occurred but was corrected in 30 days: $14,232 to $71,162 per violation; calendar-year cap: $2,134,831.
Tier 4 — Willful neglect, occurred but was not corrected in 30 days: $71,162 to $2,134,831 per violation; calendar-year cap: $2,134,831.
Criminal penalties:
Criminal prosecution is distinct from civil CMPs. HHS may impose a criminal penalty where a person or organization knowingly obtains or discloses individually identifiable health information and in doing so violates the law:
- Knowingly obtaining or disclosing PHI: Up to $50,000 and/or up to 1 year in prison.
- Offense committed under false pretenses: Up to $100,000 and/or up to 5 years in prison.
- Offense committed with intent to sell, transfer or use PHI for commercial advantage, personal gain, or malicious harm: Up to $250,000 and/or up to 10 years in prison.
Criminal cases are managed by the Department of Justice; criminal liability typically means there must be a showing that the individual engaged in knowing or intentional misconduct, and criminal liability is very fact-specific.
Also, once a HIPAA violation has occurred, your business will be listed in OCR's "wall of shame," noting the details of the violation (penalty amount, date, number of people affected).
{{blog-cta-1}}
HIPAA Compliance Checklist: Key Steps 2025
A HIPAA compliance checklist is a method for organizations to determine whether they are following the Health Insurance Portability and Accountability Act (HIPAA).
It acts as a way to identify weaknesses in their information security and privacy process, understand their obligations, and know how to evaluate if they comply.
In short, it is a path to getting and maintaining HIPAA compliance.
Who must comply?
HIPAA applies to two main categories of entities:
Covered Entities:
- Healthcare providers (doctors, hospitals, clinics, pharmacies)
- Health plans (insurance companies, HMOs)
- Healthcare clearinghouses (billing services)
Business Associates:
- IT vendors' entity handling PHI
- Medical transcription companies
- Cloud storage companies
- Legal firms with healthcare clients
- Accounting firms with healthcare billing
Even if you're a small practice with one single employee, if you transmit any health information electronically for billing or other purposes, you must comply.
Under HIPAA's Final Rule, both covered entities and business associates are considered regulated entities, expanding compliance responsibilities across all organizations involved.
HIPAA Compliance Checklist: 8 Key Areas to Cover
Whether your organization is new and starting from scratch or you are revising your policies and procedures for 2025, this checklist lays out the steps you need to take to be compliant and audit-ready.
Here is a high-level overview of the eight areas all organizations should address:
- Conduct a thorough risk assessment of each of your systems, vendors, and safeguards in connection with PHI.
- Ensure that all components of administrative, physical, and technical safeguards are developed and securely maintained.
- Ensure your patients timely access to their health information and thoughtfulness, with clear communication and options.
- Train your personnel about HIPAA compliance, handling data, and responding to data breaches routinely.
- Develop a written incident response plan and develop breach notifications using federal timelines.
- Monitor compliance with audits, penetration testing, and vulnerability scans, continually.
- Review or update the Business Associate Agreements for compliance with current HIPAA requirements.
- Use and keep all documentation of your HIPAA activities for at least six years to make audits more manageable.
Additionally, ensure that physical security and physical security controls are in place to protect PHI, such as restricting facility access and securing sensitive storage areas.
Throughout all these steps, it is essential to protect PHI by implementing and maintaining robust safeguards and policies.
How to Implement the Checklist?
Organizations embarking on HIPAA compliance must follow a systematic process. It is similar to evaluating the current environment, instituting required safeguards, and continuing compliance forever.
Develop an implementation plan with required milestones and allocation of responsibilities. Most organizations will be able to implement basic compliance in 90 days. However, maintaining compliance is a never-ending endeavor.
For example, a physical therapy clinic developed its checklist and began to meet those requirements by providing staff training (Weeks 1-2), updating their policies (Weeks 3-4), establishing technical safeguards (Weeks 5-6), and conducting their first internal audit (Week 8).
To achieve compliance, the clinic previously used a methodical approach and will continue to monitor its activities to maintain compliance with HIPAA regulations.
Common Compliance Pitfalls to Avoid
Training, Audits & Breach Response
Understanding HIPAA compliance is not simply about your systems; it is about your people being trained, your processes being regularly audited, and your staff being able to respond adequately when there is a breach.
Continuing HIPAA compliance endeavors that include ongoing risk assessments, policy adjustments, and staff training are necessary for continued readiness and to ensure your organization regularly maintains its compliance with regulatory requirements.
Here's how you can effectively manage these three areas:
Effective Training Programs & Audit Schedules
All workforce members, clinical and administrative staff, and contractors need to be trained on how to manage Protected Health Information (PHI), as required by HIPAA.
But one-time training isn't sufficient. You can conduct training, but if there is no ongoing education and regular auditing to find the vulnerabilities identified before a violation occurs, you are asking for problems.
What to do:
Conduct Initial HIPAA Training for all Staff
- Provide staff with comprehensive onboarding training on the Privacy, Security, and Breach Notification Rules.
- Tailor the training material to the training audience based on their immediate job roles (i.e., IT security vs. front desk staff).
- You need to make sure everyone has an understanding of what "PHI" is and how to deal with it.
Conduct Annual Refresher Training
- Provide all staff with annual refresher training covering primary HIPAA principles.
- Include an understanding of any new threats, tools, or regulatory changes.
Audit Completion of Training
- Maintain a log of the training (who, when, and what was included).
- Audit the signed acknowledgment from each workforce member for compliance tracking.
Establish an Internal Audit Schedule
- Conduct some form of an internal audit at least once a year (the more frequent the better, unless there is a major operational change).
- Incorporate internal reviews of access logs, device security, third-party compliance, and risk assessment programs.
Steps to Take When a Breach Occurs
- Activate Your Incident Response Plan
- Appoint an incident response team and staff with specific roles to ensure that all elements of breach response and notification are addressed adequately.
- Identify and record the type of breach and the nature of the breach.
- Contain and Mitigate the Breach
- First, contain the systems or devices related to the breach.
- Stop unauthorized access! You have to remediate any weaknesses and describe the breach.
- Notify Individuals Affected
- In the event an individual’s PHI was breached, you will need to notify the affected individuals within 60 days of discovering it.
- Your notification needs to include a clear description of the breach, what was breached, and what actions the patients need to take to safeguard themselves.
- Notify HHS (OCR)
- You should notify the Officer for Civil Rights if you have a breach involving 500 or more individuals within 60 days of the breach.
- If the breach has affected in total of less than 500 individuals, then you will need to submit an annual report regarding the same specifics noted above.
- Review and Update Policies
- After a breach, conduct the entire process of reviewing what occurred. You need to create an audit report to record findings, violations, and remedial actions.
- Review your risk management strategies, policies and procedures, training materials, and access controls based on what you have learned.
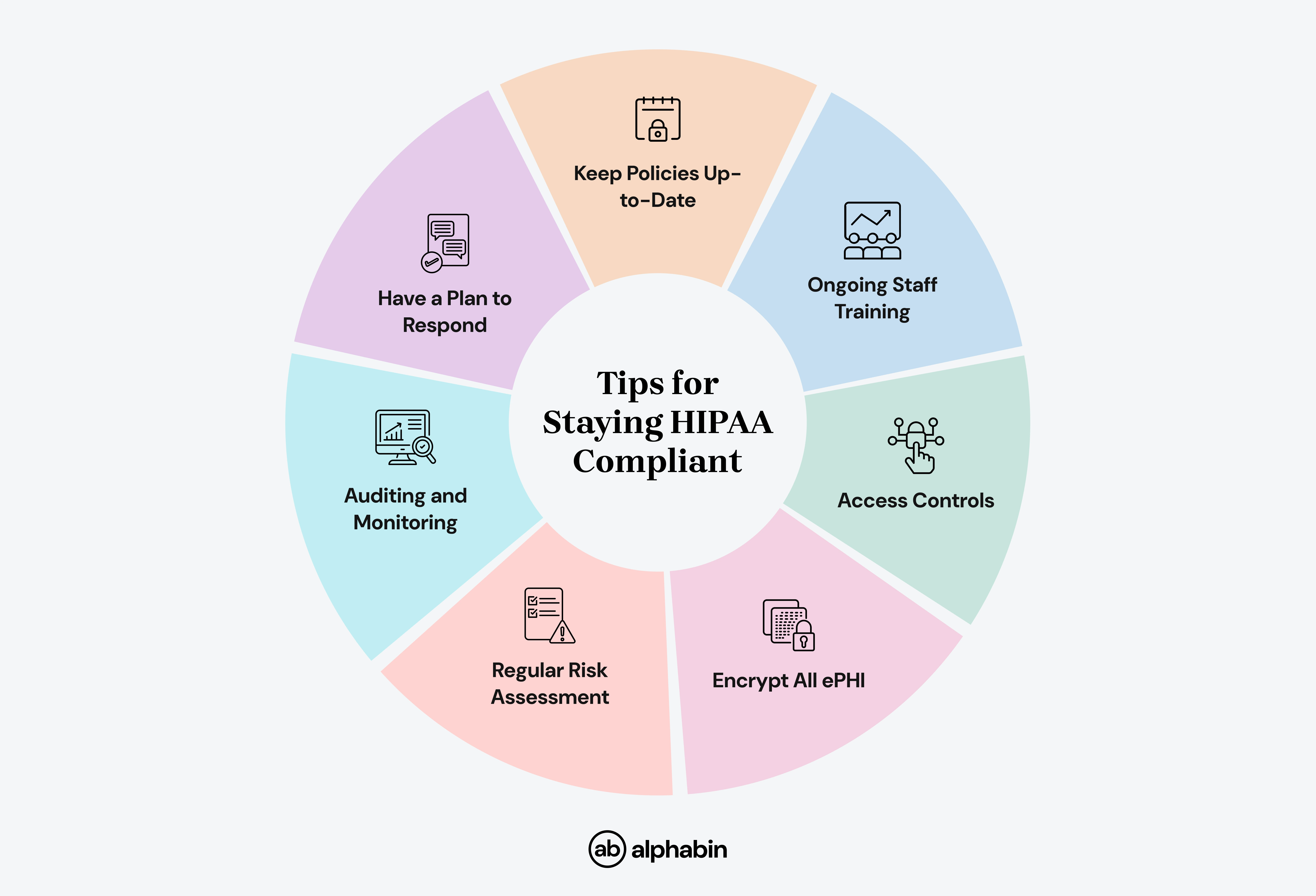
Tips for Staying HIPAA Compliant in 2025
The following tips are necessary protocols for every healthcare provider to follow if you are going to remain HIPAA compliant and avoid costly violations in 2025: