Imagine a fast-growing SaaS startup finally wins a major healthcare client. Excitement fills the room until they are hit with a reality check: without meeting HIPAA compliance requirements, they can’t legally handle patient data.
For SaaS companies, this isn’t just about compliance, it’s about building HIPAA compliant SaaS solutions that clients can trust.
Out of nowhere, the deal goes from being an innovation deal to being a survival deal. Without following this regulatory process, they stand to lose the account, and financial penalties could escalate upwards of $1.5 million per violation!
For any SaaS provider wanting to do business in healthcare, one of the longest standing sectors of the U.S. economy, it is inconceivable to ignore the implications of being HIPAA compliant. It’s the difference between unlocking opportunity and facing costly setbacks.
What is HIPAA Compliance for SaaS?
There are four components of HIPAA compliance for SaaS: privacy, security, breach notification, and enforcement.
These components guide providers in the handling of their patients' data, often referred to as Protected Health Information (PHI).
For SaaS providers, the HIPAA compliance requirement is more than just protecting the data. It means building secure systems, complying with a legal and regulatory framework, to provide healthcare clients with the assurance that the sensitive information of their patients is being protected.
While the SaaS company often acts as a Business Associates of healthcare providers (covered entities) and likely has a BAA (Business Associate Agreement); a legal contract of how the information is stored, shared, and protected.
{{cta-image}}
Why do SaaS companies need to comply?
SaaS companies must comply with regulations to manage risk, avoid fines, and ensure the security of sensitive customer data from breaches and misuse. Ensuring robust data security is essential to protect patient data from unauthorized access and maintain compliance.
Complying with regulations earns customer trust, which matters because many users will not use a product that is not compliant. Many healthcare clients will not contract with SaaS vendors lacking robust HIPAA compliance requirements.

{{blog-cta-1}}
Key HIPAA Principles
1. Privacy Rule
Sets standards for how PHI can be used and disclosed. SaaS providers must follow the “minimum necessary” rule, ensuring only essential data is accessed or shared.
2. Security Rule
Requires reasonably secure administrative, technical and physical safeguards for electronic PHI (ePHI). Risk assessments, encryption, access controls and secure infrastructure are all required.
3. Breach Notification Rule
The HIPAA Breach Notification Rule requires notification of all breaches of PHI to affected persons, HHS, and the media in some instances, usually within 60 days of detection.
4. Enforcement Rule
Describes how HIPAA rules and regulations can and will be enforced and provides penalties. Non compliance can lead to severe penalties, including jail time in the most serious violations.
Non compliance can lead to severe penalties, including jail time in the most serious violations.
Core HIPAA Compliance Requirements for SaaS
HIPAA compliance requirements should be a top priority for your SaaS business that operates with PHI. If you're working with PHI in your application, infrastructure, and data storage, they must comply with HIPAA as part of an effective compliance program.
Basic HIPAA compliance for SaaS includes:
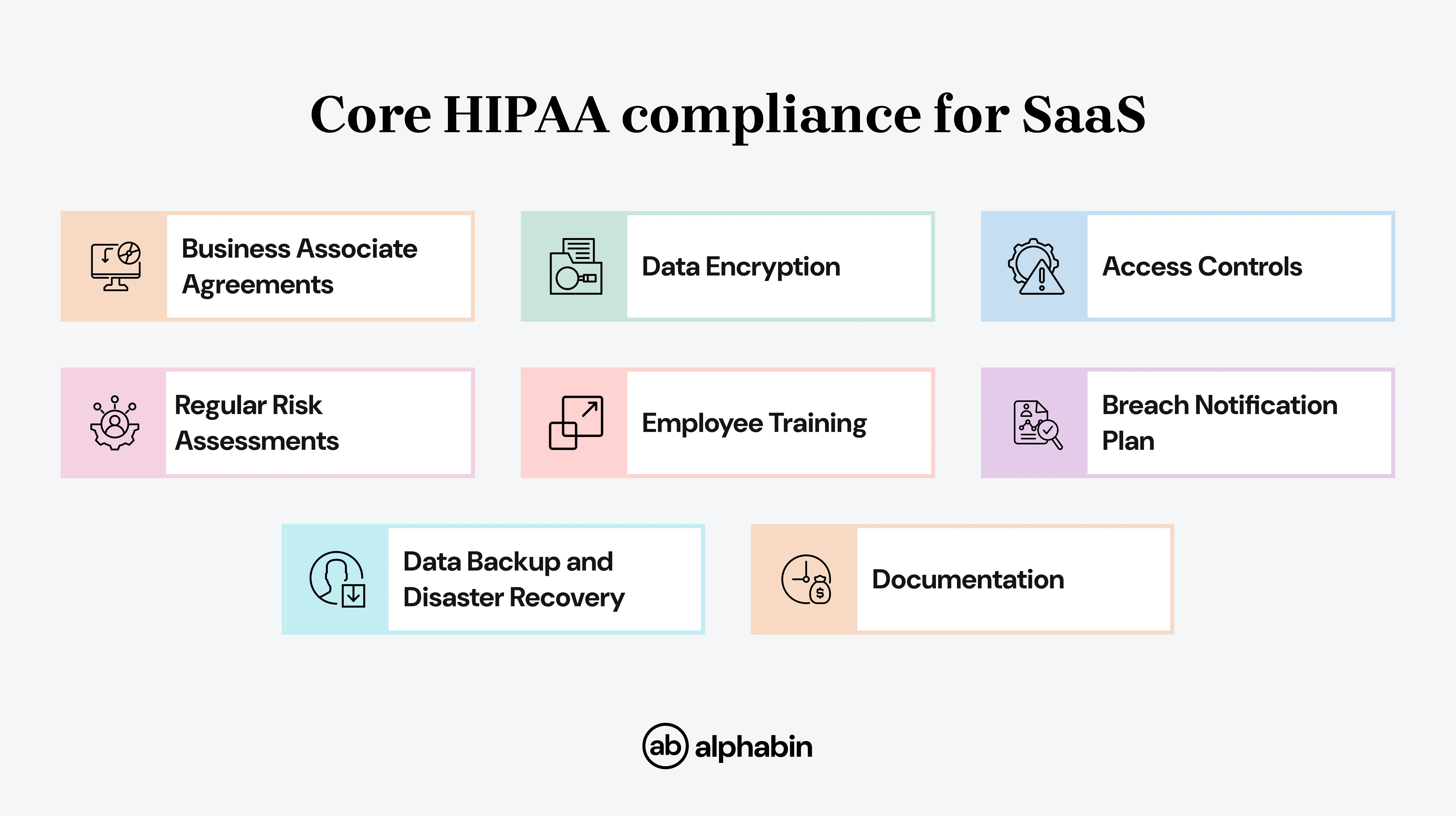
This acts as a practical SaaS HIPAA compliance checklist for providers.”
Technical, administrative, and physical safeguards
To comply with HIPAA, SaaS providers must have three pillars of safeguards, which form the HIPAA security requirements for SaaS providers.
These requirements apply not only to SaaS providers but also to other covered entities such as healthcare clearinghouses and group health plan administrators.
{{blog-cta-2}}
Business Associate Agreements (BAA): The Legal Backbone for SaaS
Under HIPAA, covered entities and their business associates are required to have a Business Associate Agreement (BAA).
A BAA is a legal contract that obligates business associates (such as SaaS providers) to treat and protect Protected Health Information (PHI) appropriately conformed to HIPAA standards.
The covered entity creates and maintains PHI, and both parties must adhere to mandated HIPAA privacy requirements.
What is a BAA and why it matters
A BAA (Business Associate Agreement) is a legal contract between the "covered entity" (the healthcare provider) and the "business associate" (a third-party vendor).
A BAA identifies roles and responsibilities for both parties in relation to protecting patient Protected Health Information or PHI.
BAAs are mandatory under HIPAA. No BAA = No legal basis to handle PHI for U.S. healthcare clients.
The BAA details permitted uses of PHI, required safeguards, reporting requirements for breaches, and liabilities.
Why does BAA matter?
For the healthcare provider (covered entity):
- Ensures compliance: Sharing PHI without a BAA is a breach of HIPAA and will result in significant legal and financial penalties from the U.S. Department of Health and Human Services (HHS).
- Limits liability: A BAA clarifies that a business associate is legally responsible for safeguarding PHI. This can limit a covered entity's liability in the event of a vendor breach.
- Outlines responsibilities: The contract stipulates what the vendor can do with PHI. A BAA clearly defines the responsibilities related to the permitted uses and disclosures of PHI around the vendor's use of snag.
- Mandates breach reporting: It requires the vendor to notify the covered entity immediately after a data breach so the parties can act quickly.
For the third-party vendor (business associate):
- Legal necessity: For any business using PHI on behalf of a covered entity, a BAA is required to legally access this information.
- Defines scope of use: The BAA defines what the vendor can and cannot do with the PHI. It provides guidance with a legal framework.
- Extends accountability: The BAA requires that, if the business associate uses subcontractors, the subcontractors must also abide by the same HIPAA rules. The contract creates a chain of accountability.
- Protects reputation: HIPAA compliance through a business associate agreement protects the vendor's reputation and shows it is committed to patient privacy.
{{cta-image-second}}
Achieving HIPAA Compliance for SaaS
Stepwise plan to get SaaS HIPAA compliant
1. Identify and Map PHI Flows
- What to do: Document where Protected Health Information (PHI) is collected, stored, transmitted, or processed across your system.
- Why it matters: A clear data map is the foundation for compliance readiness.
2. Conduct a Comprehensive Risk Assessment
- What to do: Review for vulnerabilities (e.g., obsolescence software, internal mishandling, external threat), and determine threat impact.
- Why it matters: This HIPAA compliance risk assessment for SaaS ensures vulnerabilities are identified and addressed before they become liabilities.”
3. Remediate Gaps
- What to do: Address all identified risks, fix vulnerabilities, patch systems, tighten access controls.
- Why it matters: Demonstrates proactive compliance and reduces liability.
4. Implement Required Safeguards (Technical, Administrative, Physical)
- Technical: Encrypt PHI, use role-based access controls, enable logging/auditing, secure authentication, and secure transmission (e.g., TLS).
- Administrative: Appoint a HIPAA Security Officer, train workforce, define access management, conduct awareness training, and establish contingency plans.
- Physical: Securing your facilities, workstations, devices, managing media per HIPAA standards.
5. Sign and Maintain Business Associate Agreements (BAAs)
- What to do: Establish BAAs for clients and vendors who are accessing PHI (whether hosting, backups, or otherwise).
- Why it matters: Legally binding agreements that clarify HIPAA responsibilities and protections.
6. Develop Incident Response & Breach Notification Plan
- What to do: Create a process for incident response that outlines the steps: detection, containment, investigation, remediation, and notification.
- Why it matters: Ensures timely and compliant breach management.
7. Document Policies & Conduct Regular Audits
- What to do: Maintain written policies, logs, training records, and audit trails. Perform regular internal/external audits.
- Why it matters: Keeps compliance proactive, verifiable, and evolving with threats or operational changes.
8. Continual Monitoring and Improvement
- What to do: Update risk assessments, review and adapt policies, monitor vendors, and conduct ongoing staff training.
- Why it matters: HIPAA compliance isn’t a one-time goal; it’s an ongoing journey.
Practical Tips and Common Mistakes
How to choose HIPAA-ready vendors
Phase 1: Pre-Selection Vetting
- Always enter into a Business Associate Agreement (BAA)
- Review the BAA for data use, subcontractors, and breach notifications.
- Request proof of compliance (HITRUST, SOC 2 reports).
- Request risk assessments, policies, and client references.
- Make sure they have a HIPAA officer and staff are trained.
- Verify encryption, MFA, role-based access, and audit logs.
- Verify data center security and restricted access controls.
- Review the breach response plan and disaster recovery plan.
Phase 2: Post-Selection Monitoring
- Establish a vendor risk management program.
- Conduct audits of vendors periodically, more frequently for high-risk vendors.
- Review access/information logs and audit trails.
- Leverage technology to continuously monitor risk.
- Verify subcontractors have BAAs and manage risk.
{{cta-image-third}}
Conclusion
Achieving and maintaining HIPAA compliance requirements is not just an obligation to comply with a regulation; it establishes the foundation for trust in the healthcare sector.
For SaaS organizations, protecting the security and privacy of Protected Health Information (PHI) includes addressing every aspect of compliance, which includes key elements: technical safeguards, administrative procedures, vendor management, and ongoing oversight.
This can feel overwhelming, but the right partner will make a big difference. Alphabin simplifies this process with our specialized healthcare testing and security testing services.
Alphabin validates that your platform is HIPAA-ready, secure, and trusted by both patients and providers by validating encryption and simulating breach scenarios.
FAQs
1. How does Alphabin help with HIPAA compliance?
We provide compliance checks and security reviews to ensure PHI is secure, access is controlled, activities are monitored, data is encrypted, and risks are identified early.
2. What are the key features of the best HIPAA compliance tools in 2025?
The best HIPAA compliance tools include risk management, audit readiness reports, continuous monitoring, and HIPAA-specific control libraries. These features streamline compliance and protect sensitive patient data.
3. Why should healthcare providers use HIPAA compliance automation software?
HIPAA compliance automation software reduces manual audits, saves hundreds of hours, and minimizes human error. It ensures faster compliance readiness and stronger protection against costly data breaches.
4. How do I choose the right HIPAA compliant software solution?
Choose HIPAA compliant software that supports administrative, physical, and technical safeguards with strong vendor risk management. Look for tools that fit your organization’s size, IT complexity, and compliance needs.



.svg)









%20(1).webp)