You just landed your biggest deal ever. An enterprise client is ready to sign a million-dollar deal, but there’s one non-negotiable: they need your SOC 2 report in 90 days.
Now you’re in trouble. Internal controls, access policies, logging, vendor due diligence it all hits at once. The team is Googling terms like “SOC 2 Type II” and “audit readiness,” trying to make sense of what feels like a regulatory jungle.
This happens every day in fast-growing SaaS companies. Not because teams lack effort, but because they lack a clear, actionable SOC 2 checklist.
Without the checklist, the audit gets delayed, teams become frustrated, and growth slows down. But the right checklists can turn your confusion into clarity.
This guide will help you solve all your doubts, troubles, and you will be able to pass SOC 2 compliance with confidence.
What is SOC 2 compliance?
SOC 2 stands for Service Organization Control 2 and is a framework developed by the American Institute of Certified Public Accountants (AICPA).
SOC 2 specifies how organizations, like SaaS organizations and cloud service providers, can protect and secure customer data while ensuring the security, availability, confidentiality, processing integrity, and privacy.
SOC 2 is not just a law or regulation. It is a voluntary compliance standard.
However, for some organizations that are involved in handling sensitive customer data, being SOC 2 compliant is now effectively a business necessity, especially when working with larger businesses or in regulated industries
Why do SOC 2 compliance checklists matter?
A SOC 2 compliance checklist is useful because it provides organizations a reasonable and attainable path to demonstrate they care about data security and privacy - creating trust in customers and partners.
{{blog-cta-1}}
Preparing for SOC 2
Achieving SOC 2 compliance requires some preparation. Getting audit-ready will take several months of preparation, planning, and checking a massive checklist.
As part of this process, conducting a gap assessment helps identify areas that need improvement before the audit.
Before you go digging into the SOC 2 checklist, you should define what the audit will cover. Defining the audit scope prevents wasted effort and will help ensure you have a successful audit.
Define Scope and Objectives
The SOC 2 scope defines the specific systems, data, and controls that a service organization will be evaluated on during a SOC 2 audit.
It describes the boundaries of the audit so that the organization will know which parts of its operations and infrastructure fall under the SOC 2 criteria. The scope should include all of the organization's systems that process or store customer data.
Also, identify the systems, services, teams, and infrastructure that store or process customer data. Only include what’s relevant; too broad a scope can increase cost and complexity.
Objective of SOC 2:
- To demonstrate that a service organization manages customer data securely and effectively with “trust service criteria”, security, availability, processing integrity, confidentiality, and privacy of that data.
- To ensure the effectiveness of the organization's controls in meeting the trust service criteria.
- To decide why you are getting SOC 2? Is it to meet customer requirements? Enter enterprise markets? Or improve internal security?
- Your objective will determine how you prioritize controls and timelines.
Best Tools to Use for SOC 2 checklists
Instead of doing SOC 2 compliance manually, consider using specific tools to automate your compliance program.
The correct compliance automation tools will eliminate a lot of the manual, time-consuming, and resource-intensive repetitive tasks performed throughout the compliance process.
Such as gathering evidence, performing risk assessments, managing policies, reviewing user access, managing vendor risk, and preparing for an audit.
The Ultimate SOC 2 Checklist
A SOC 2 checklist is your roadmap to compliance. Without proper management, teams miss requirements or waste time on unnecessary activities.
To ensure comprehensive coverage, your SOC 2 checklist should include business processes and control activities, so that all relevant workflows and specific controls are addressed.
What should be in the SOC 2 checklist?
An SOC 2 checklist should be related to the 5 Trust Services Criteria (Security, Availability, Confidentiality, Processing Integrity, and Privacy) and the controls required to meet those criteria.
{{cta-image}}
Your SOC 2 checklist should cover 5 main areas:
- governance and risk management,
- security controls implementation,
- documentation and evidence collection,
- audit preparation.
- Third-party risk management.
Start with policy development; you’ll need information security policies, incident response procedures, vendor management protocols, and employee training programs.
Internal control is a foundational element of SOC 2 compliance, ensuring that your policies and procedures are effective and meet audit requirements.
SOC 2 compliance checklists: Step-by-step
1. Define your scope
What to do: Make a list of all systems, processes, people, and third-party services in your and your customer’s organizations that interact with customer data.
How to do it: Start with how the data flows through your product and in your infrastructure. You will want to include backend services, integrations, the DevOps pipeline, and any 3rd Party tools etc.
2. Choose Trust Services Criteria (TSC)
What to do: Choose the SOC 2 principles that apply to your product.
How to do it: Security is always required. Choose Availability if you offer uptime or SLAs. Add confidentiality if you handle sensitive or proprietary info.
Include Privacy only if you collect personal or regulated data (like GDPR or CCPA). AICPA guidance is a good reference, or have a consultant assist if you are uncertain.
3. Perform a Risk Assessment
What to do: Identify potential threats and vulnerabilities to systems, data, or operations.
How to do it: Evaluating risks is an important part of the process. Document potential threats. Consider all forms of threat, including unauthorized access, loss of workstation data, downtime, etc.
Assess the likelihood of each of the potential threats occurring and determine how serious a threat/impact it would represent.
4. Build Internal Security Controls
What to do: Build technical and procedural defenses to help reduce risk.
How to do it: Implement controls that address the identified risks. Use least privilege or have IAM tools to help you with least-privilege e.g.; AWS IAM and Okta.
Enforce MFA for all systems. Define change management through code reviews and approvals.
5. Implement the documentation process
What to do: Document your security policies and how controls work.
How to do it: Use a shared space, like Notion or Confluence, to capture information. Write short policies on data access, onboarding, vendor management, and incident response.
6. Monitoring and Logging
What to do: Log access to systems and sensitive operations.
How to do it: Log across cloud infrastructure, apps, and tools. Use Datadog, Panther, or native cloud logs.
Monitor for login anomalies, permission changes or file access. Use monitoring tools to detect vulnerabilities in your systems. Store logs for 12+ months and review periodically or during incidents.
7. Conduct readiness Assessment
What to do: Test your audit readiness before the auditor comes.
How to do it: Run a self-assessment with an SOC 2 checklist. Or use Vanta or Secureframe to automate it. Identify and remediate control gaps in documentation, logging, or control coverage. Evaluate the operational effectiveness of your controls during this assessment.
8. Select an auditor
What to do: Hire a CPA firm with SOC 2 experience to do your audit.
How to do it: Choose a firm that knows SaaS products and cloud infrastructure. Look for Prescient Assurance, BARR Advisory, or A-LIGN.
Ask about their experience, tools, and audit process. Request a sample report and check client references if needed.
{{cta-image-second}}
9. Schedule Your SOC 2 Audit
What to do: Decide the type of audit, how soon you will do it, and your evidence collection methodology.
How to do it: A Type I audit will mean testing controls at one point in time; a Type II audit will mean reviewing controls over a period of time.
There is a mandatory observation period, which is the time it takes from completing a Type I audit to commencing a Type II audit, during which ongoing monitoring continues to provide direct evidence that the controls are still effective.
10. Remediate Gaps and Issues
What to do: Remediate any gaps in controls that were identified in the readiness or audit.
How to do it: You should track gaps via a ticketing system like Jira. You may want to assign owners to each identified gap; this will provide accountability, and you can specify timelines for remediation.
Streamlining SOC 2 for SaaS Teams
Numerous SaaS teams undertake SOC 2 compliance reactively and, as such, create a confrontation that often leads to avoidable stress or inefficiencies.
Understanding how to avoid common pitfalls and applying more efficient workflows can greatly reduce the amount of heavy lifting your team does.
If you have designated a compliance manager who manages the overall process with all of the requirements across the board in mind, you'll have a smoother process.
Evaluating the compliance posture of your organization on a regular basis is a tremendous way to keep yourself away from challenges and to maintain readiness for SOC 2 compliance.
SOC 2 mistakes SaaS teams make
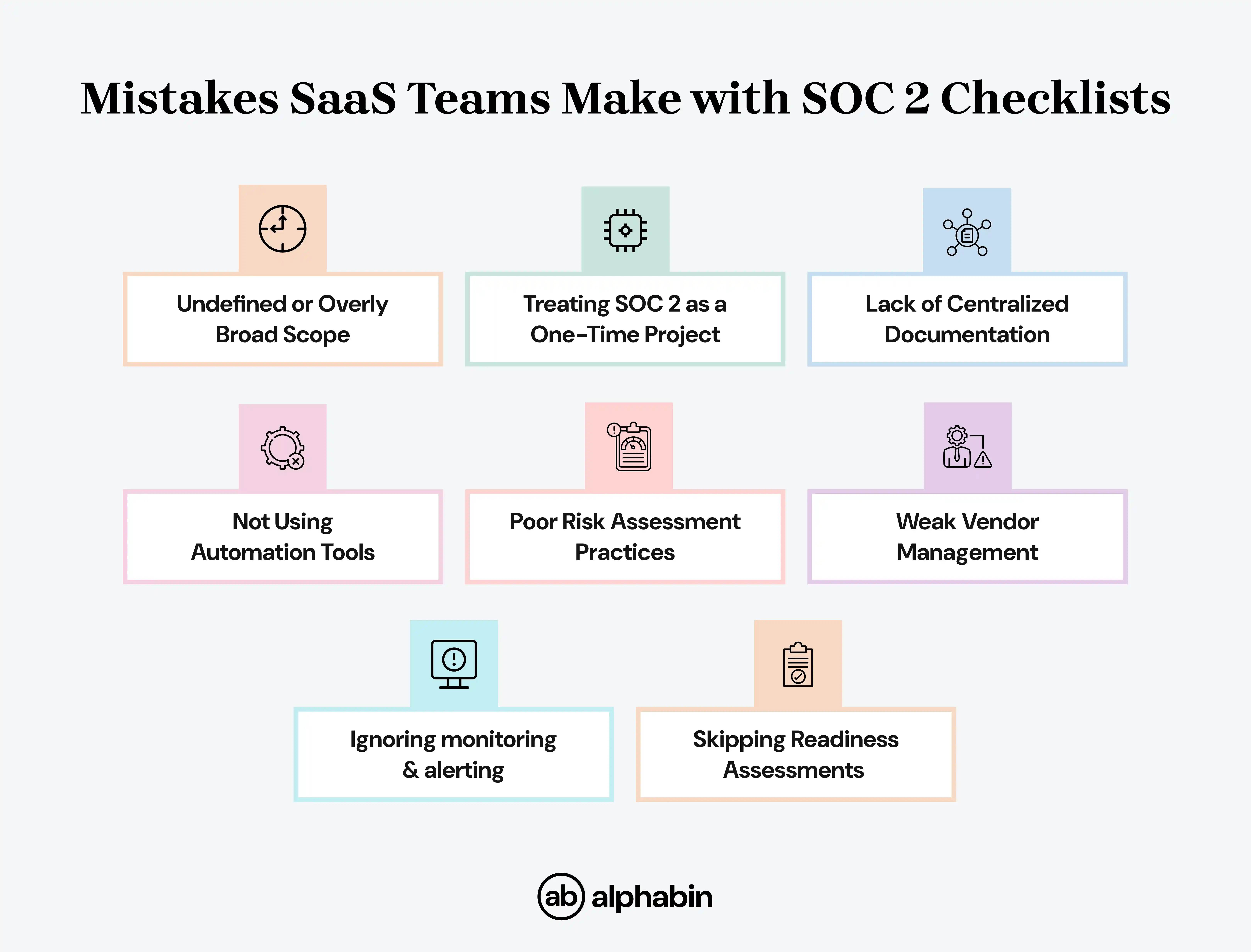
Tips to streamline the process
1. Start with a Readiness Assessment
Do a gap analysis before you even engage an auditor. Use internal checklists or tools like Vanta, Drata, or Secureframe to find missing controls early. So you don’t get surprised during the actual audit.
2. Use Compliance Automation Tools
Streamline evidence collection, control tracking, and policy monitoring. You can use 3rd party tools like Vanta, Drata, and Scrut that integrate with AWS, GitHub, G Suite, Okta, and other services to collect audit logs, access reviews, and system configurations.
Make sure organization controls are embedded in your routine system operations to maintain compliance and support ongoing audit readiness..
{{blog-cta-2}}
3. Limit and Clearly Define Scope
Don’t overcomplicate by including every tool or service.
Focus only on systems that touch customer data. Document what’s in-scope vs out-of-scope and review it with your auditor early.
4. Centralize Policies and Documentation
Use a single, shared resource (Notion, Confluence, or Google Drive) for all documentation related to compliance.
Have version control, assign document owners, and organize the documents process by TSC (Trust Services Criteria) to ensure audit-friendly documentation.
5. Assign a Compliance Owner
Appoint an individual (Ops, Engineering, or Security) to be the SOC 2 owner.
This individual will act as an intermediary between teams, manage tools, track deadlines, and communicate on behalf of the company with the auditor.
6. Integrate Security into Daily Workflows
Make security and compliance second nature. Incorporate action items in GitHub PR (pull request) templates for change control, use Slack workflows for access requests, and use ticketing tools (like Jira) to log controllable activities.
Post-Audit: What’s Next
- SOC 2 is a Continuity Process: Most customers (on average) expect a SOC 2 Type II report, once annual re-issue is standard. Service organizations establish trust with their clients through repeated engagement on SOC 2 reporting and tightening up engagement in the compliance assessment process.
- Plan On Compliance Reviews: Setting a continuous compliance review quarterly will allow an organization to consider itself audit-ready for 12 months of the year.
- Keep collecting evidence: Continue to collect audit evidence continuously (logs, access records, policies)
- Update As You Go: Update your policies and controls as changes take place in your systems or tools, or team structure.
- Assess change: Assess any new system or process on the basis of SOC 2 before implementation.
- Track: Keep tabs on growing expectations as compliance and frameworks evolve. Also, keep timely and accurate reporting for financial benefit, ongoing compliance, or audit at the additional touch point along the journey.
Conclusion
Attaining SOC 2 compliance is an important milestone — but maintaining compliance is where the hard work (and trust) starts.
For SaaS teams, it is not merely about preparing for an audit; it requires developing a scalable culture of security, accountability, and operational excellence throughout the company.
At Alphabin, we’ve partnered with high-growth software companies to not only get ready for SOC 2 compliance but also work with them to embed quality assurance and security practices into their processes in a sustainable way.
{{cta-image-third}}
Including gap identification, control testing, effectiveness, and automating evidence collection, we provide companies the level of technical depth that modern SaaS teams need to move exceptionally fast — without cutting corners.
If you're preparing for SOC 2 or looking to reduce the complexity of ongoing compliance, partner with Alphabin and make compliance a competitive asset rather than a burden.
FAQs
1. Can small SaaS startups become SOC 2-compliant?
Yes, but they should think of automation tools and start with Type I audits.
2. How long is an SOC 2 report good for?
An SOC 2 Type II report is typically good for 12 months.
3. How long does it take to achieve SOC 2 compliance?
Typically, 6–12 months. With strong security practices, you might only need 4–6 months.
4. What if we fail the SOC 2 audit?
You'll receive a list of issues to resolve, and when you resolve them, the auditor can re-test and may only delay your report.



.svg)










.jpg)
